What if we said you might be sitting on value you don’t even know is there? Now what if we told you that there is value in the old IT Assets and Electronics sitting in your IT closet just waiting to be replaced or upgraded?

Blog
Let’s talk efficiency
Inefficiencies in the data center can cause equipment failure leading to downtime. And this
could impact your entire business operations. Knowing what’s in your data center is the first
step toward improving energy efficiencies and reducing costs.
Make sure to ask a lots of questions
Given the complexities and manpower needs of decommissioning a data center, it’s important to hire a professional who specializes in it.
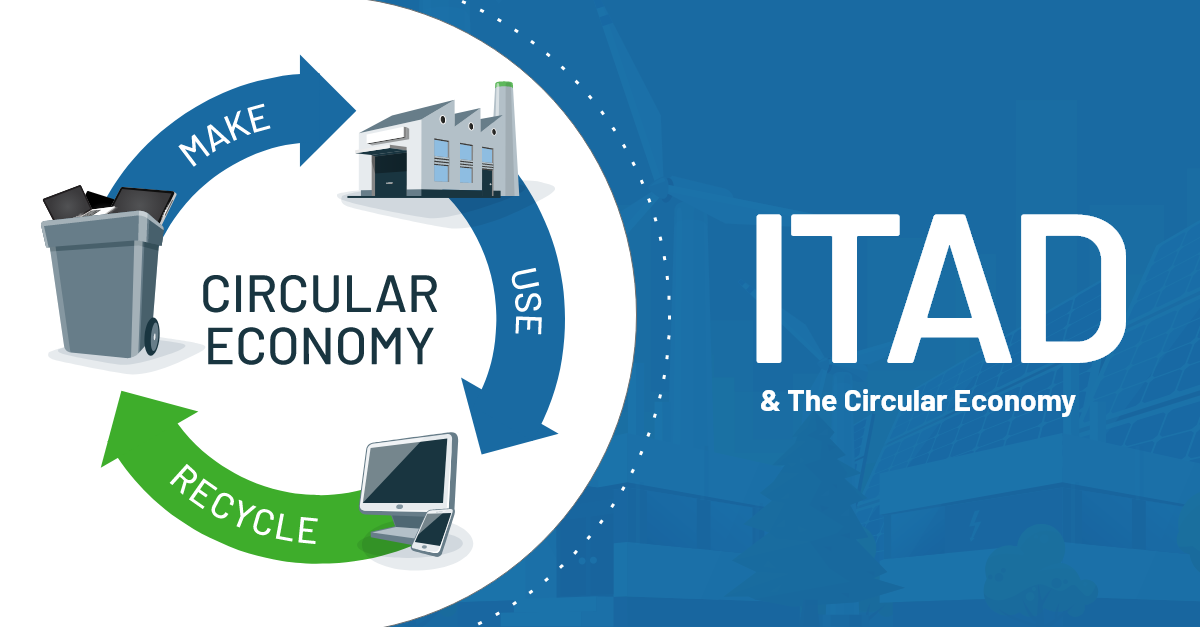
ITAD And The Circular Economy
The term “circular economy” is a rather new concept. It’s much more than just a catchphrase – it’s a totally different approach to IT Asset Disposition (ITAD), as well as waste and asset management, that ensures sustainable growth over time. A Circular Economy reduces material use, redesigns materials to be less resource intensive and recaptures “waste” as a resource to manufacture new materials and products.
off-premises. However, the process of migrating data does open up the possibility of key risks and vulnerabilities. For this reason, it is important to have a robust strategy in place for mitigating the cybersecurity risks during cloud migration.
Cloud Migration and Data Security
One of the greatest benefits of utilizing cloud-based data centers is that your organization’s data is held securely
off-premises. However, the process of migrating data does open up the possibility of key risks and vulnerabilities. For this reason, it is important to have a robust strategy in place for mitigating the cybersecurity risks during cloud migration.
What is E-Waste and why is it such a problem?
E-waste refers to electronic products that are unwanted, not working and nearing or at the end of their useful life, ie., computers, VCR’s, fax machines, IT servers and racks, and almost anything that has a battery or basic cord. Because many people don’t give much thought to where their e-waste goes, you might not know of any other way to dispose of it other than to simply throw it into the trash, which ultimately ends up in landfills – which is bad for the environment.
Earth Day
As Earth Day 2022 draws near, let’s take a closer look at how ITAD services can help organizations manage their e-waste correctly.
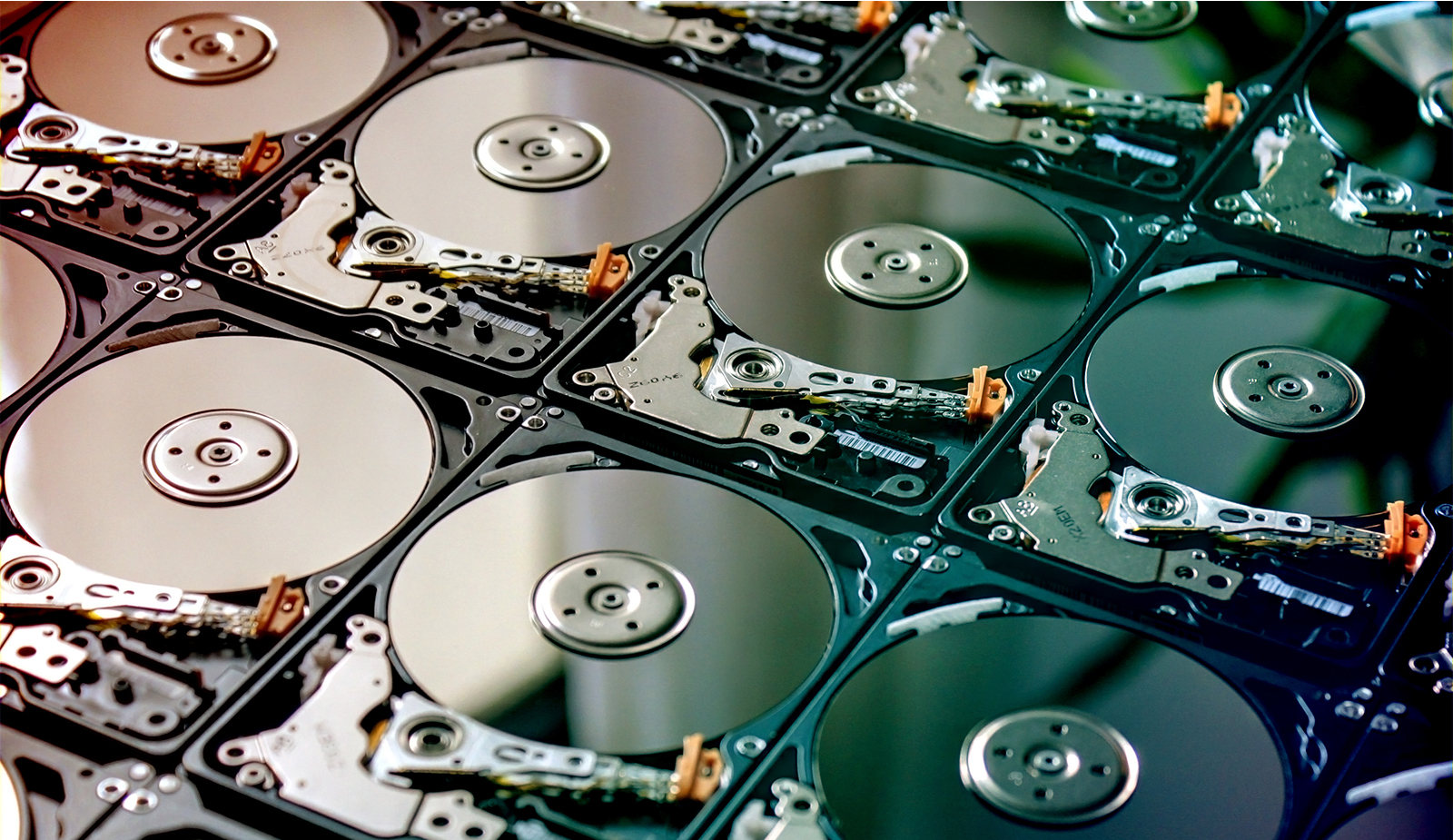
Data destruction – why it matters
The importance of destroying all data would seem to be obvious. Yet according to some studies, as many as 10% of all secondhand hard drives sold over the internet still hold personal information. And it’s not just individuals who fail to destroy all data, it’s businesses as well.
Throwing storage devices away is not an option
At OceanTech, we ensure that every data containing device receives compliant data destruction. We follow strict guidelines to ensure data security and complete risk mitigation is achieved.
The most used laptop models to work from home
In the wake of COVID 19, most companies have issued directives to work from home. Meanwhile, some of you might feel yourselves in the pressure of deciding which laptop should be purchased for working from home.
Work from home
Whether you are an independent contractor or an IT manager, COVID-19 has created quite a few new IT hardware problems for you to contend with. Thankfully, the most important ones have real and immediate solutions.
You’ve got us covered
The main component of value in a medical practice is the goodwill intangible assets which cannot be readily observed – You’ve got us covered, and we THANK YOU